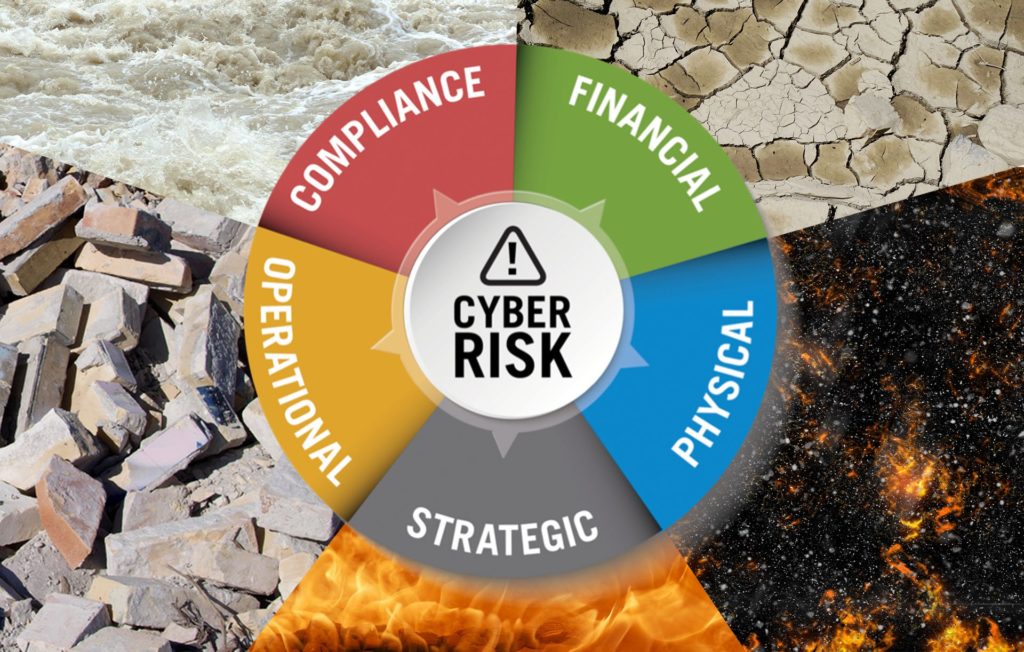
This is the concluding post in our series about cybersecurity risk. Each week for the past six weeks we discussed a different category of enterprise risk and how cybersecurity impacts those risks at the board and executive level.
Cybersecurity Seen as an Influencer to Known Areas of Risk – Lessons Learned
Over the past few weeks, we have discussed different case studies and lessons learned when evaluating enterprise-wide cybersecurity risk. We learned about financial risk and how a politically-motivated breach cost Sony more than $27 million. We discussed compliance risk and the consequences of negligence through the FTC’s lawsuit against a hotel company that was hacked three times in two years. We also studied strategic risk and how a revenge hack brought down the reputation and entire business of security firm HBGary Federal. We reviewed operational risk and saw how malware crippled Saudi Aramco’s day-to-day business operations. Finally, we explored physical risk and learned how Stuxnet, a vicious computer worm, destroyed Iranian nuclear centrifuges.
There was an overarching theme that linked all of the case studies and risk areas: Cybersecurity is a people problem, not a technology problem. As Bruce Schneier, a leading security author noted, “If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.”
Indeed, the best security solutions revolve around people. Long-term solutions are not next-generation firewalls, but training and awareness. Investment in knowledge will promote a culture of resilience in an organization. Informed leaders and skilled professionals are the most important aspects of an organization’s defense.
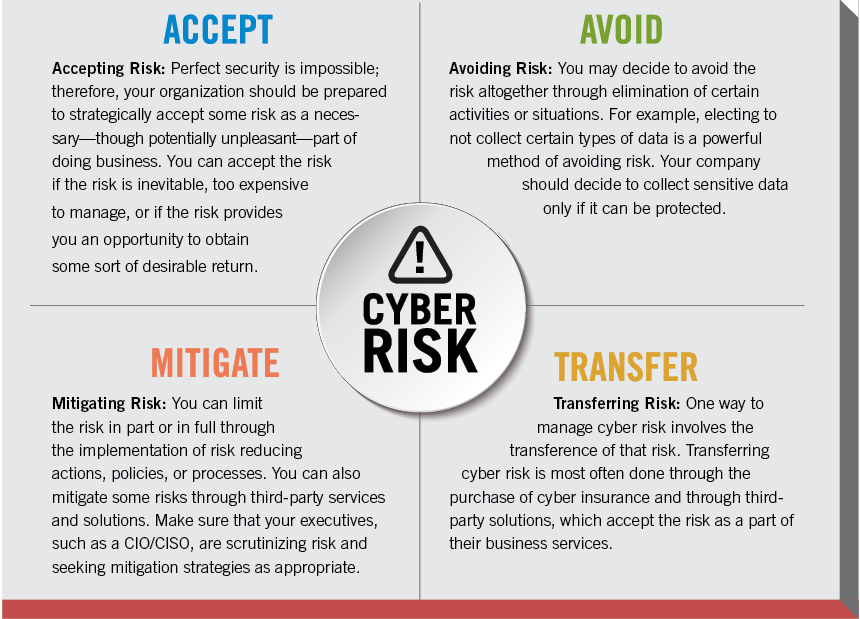
We have also discussed over the past several weeks that managing cyber risk is no different than managing other business risk categories. The risk management techniques that you are already familiar with apply to cyber risk. Like any other business risk, you have four management techniques to consider: acceptance, avoidance, mitigation, or transference.
Acceptance
Accepting some risk may be necessary, though unpleasant. You should practice this strategy if the risk is inevitable, too expensive to manage, or if it provides an opportunity for a long-term return.
Avoidance
You can decide to shut down certain activities or situations to avoid the risk altogether. For example, opting to avoid collecting certain types of data is a powerful form of risk avoidance. You should collect sensitive data only if you have the ability to protect it.
Mitigation
You can limit risk by implementing risk-reducing actions, policies, or procedures. For example, making multi-factor authentication mandatory for all log-in procedures is a policy that can make your employees’ accounts more secure.
Transference
Transferring cyber risk often takes the form of purchasing cyber insurance or a third-party security solution that accepts the risk as part of a business service.
Cyber Risk is Manageable
These four risk management practices prove that cyber risk is manageable. By presenting cyber risk in the more familiar lenses of known management practices, risk areas, industry stories, and natural disasters, we hope that we have removed some of the intimidation and confusion surrounding cyber events. By removing complexity and uncertainty surrounding these events, we hope you feel empowered to confidently learn how to manage this risk.
If you followed this cyber and enterprise risk series, then you are on a path to cyber literacy; it’s a first step in creating a cyber secure culture. Continue your journey by enrolling in one of our Cyber Resolve workshops. Our executive programs, either in a workshop setting or in your boardroom, provide engaging content that help you learn to manage cyber risk.
Take your cyber literacy to the next level. Enroll today.