Our Methodology
Our methodology sets us apart from other training providers. Using a data-driven approach, we build employee skill profiles to better align training and measure effectiveness against organizational objectives.
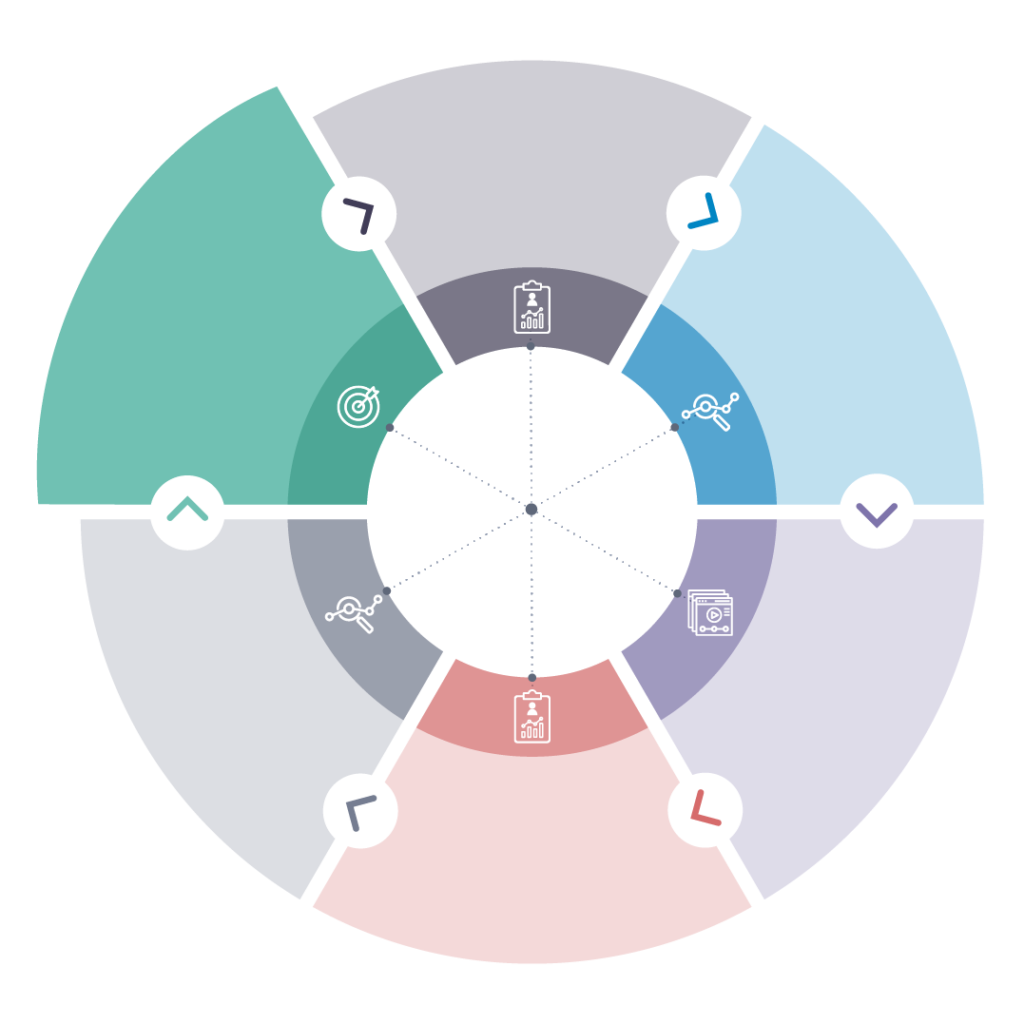
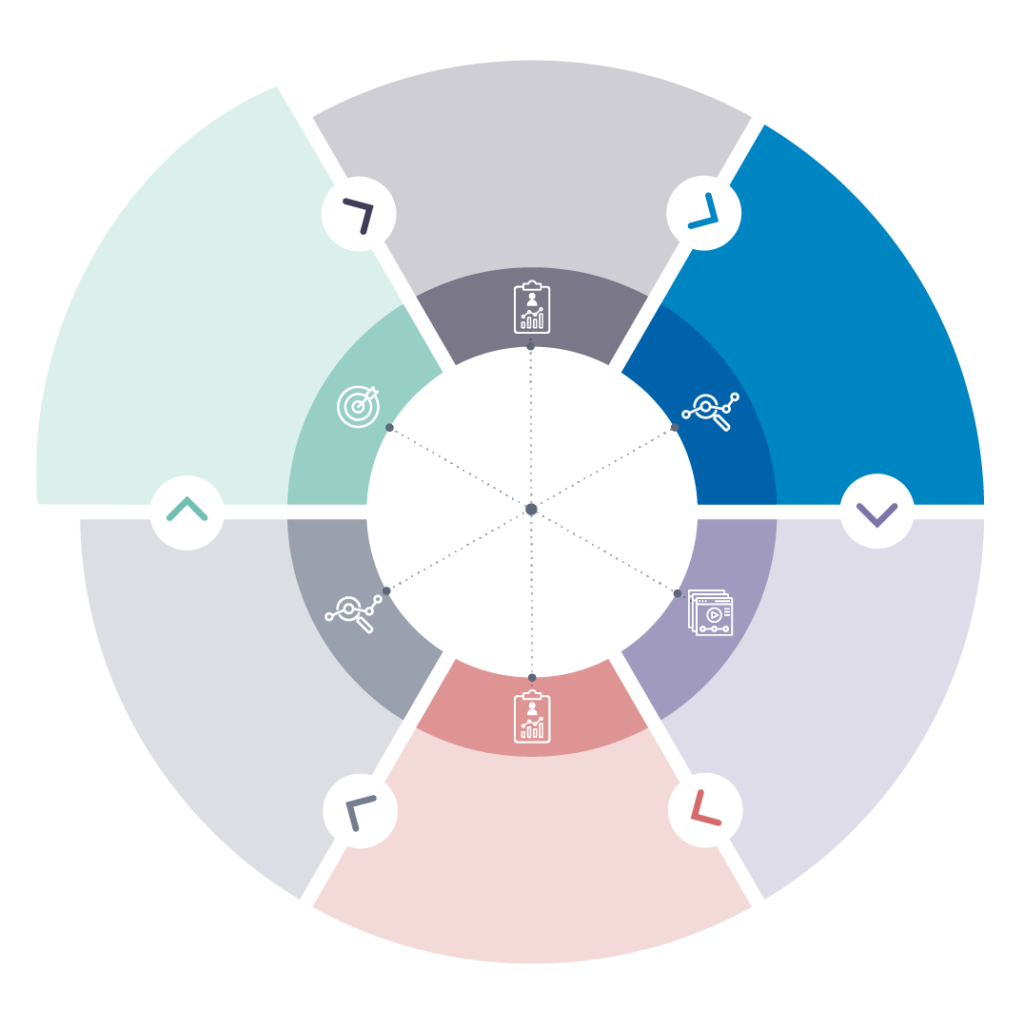
When it comes to training and workforce development, we believe it’s important to continuously assess and adjust to keep pace with the evolution of your workforce needs. Our six-step methodology is rooted in data to help inform the next step and ensure it ties back to your organization’s goals.
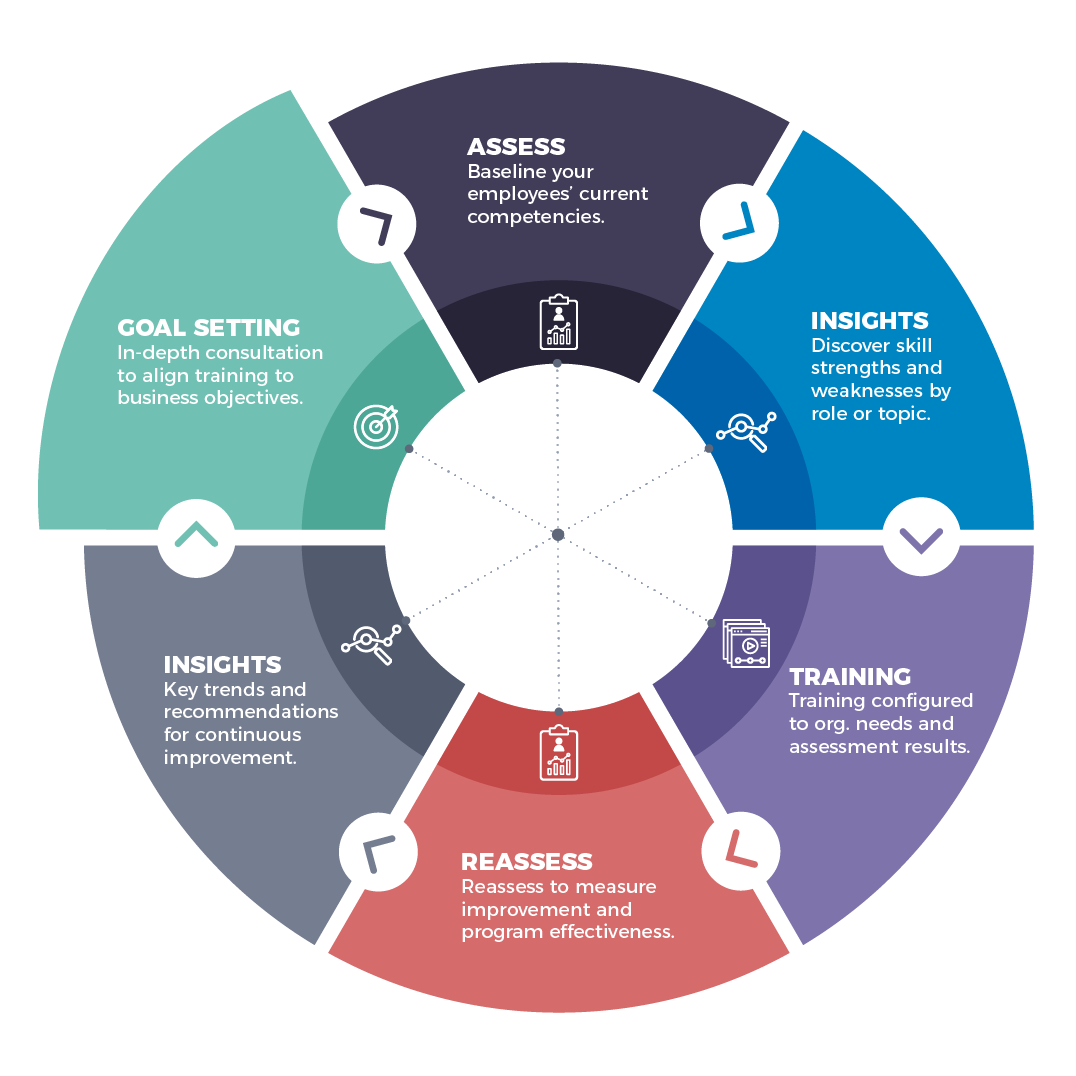
Goal Setting
An in-depth consultation to align training to business objectives. Examples include increasing certification pass rates, improving onboarding, or updating job roles.
Assess
Use diagnostic assessments to baseline employees’ current skills and competencies. Assessments are built into our comprehensive courses or use our NICE Workforce Diagnostic.
Assessment & Role-Based Training for Top US Healthcare System
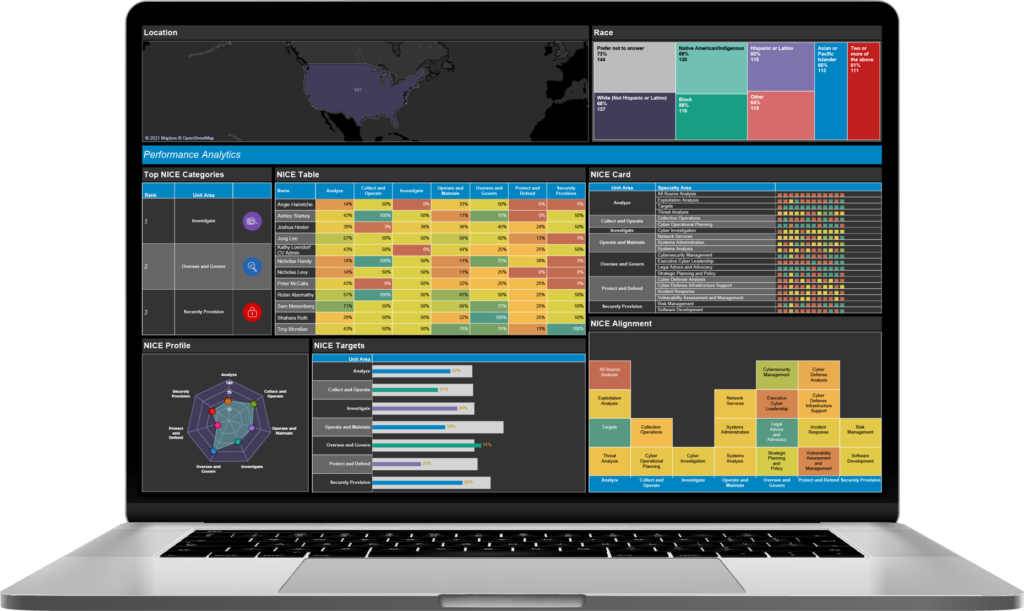
Learn how using skills diagnostic assessments and role-based cyber training helped this top US healthcare system improve employee performance and cut training spend by 40%.
Insights
Discover employee skill strengths and weaknesses by role or topic. Following the diagnostic, we create skill profiles and analyze results to uncover performance trends to guide training.
Training
We build training roadmap options with either off-the-shelf courses or a custom configured program and work with you to ensure it aligns with your schedule and organizational goals.
See the difference.
Now there’s real training data and insights to capture and prove real workforce transformation. Schedule a time to connect today.
Reassess
Reassess employees to measure improvement and program effectiveness. Final examinations are included with each comprehensive course to evaluate improvement.
Insights
Receive analysis and recommendations for continuous improvement through a detailed insights report and/or expert consultation, and receive guidance on long-term strategy.
case studies
Designed for the Individual.
Configured to the Organization.
N2K solutions are built around data, efficiency, and practicality. Regardless of your industry, we can configure a solution for you.
Connect with a Workforce Expert
You’re not alone. Organizations around the world are struggling with issues related to cybersecurity skills and talent. Fortunately, N2K can help. Fill out this form and a member of our team will touch base with you within 24 hours. Once we connect, we’ll learn more about the issues you’re currently facing and provide more information as to how we can help you and your team achieve your workforce goals.