Online Training Course
Cloud SOC
Equip your security team with the essential skills in detection, identification, and vulnerability analysis of attacks on cloud infrastructures.
Course Overview
For many organizations, the Security Operations Center (SOC) acts as the keeper of enterprise data, networks, and applications, regularly providing reports on network activity and potential threats. However, with more systems migrating to the cloud, SOC teams must be able to manage multiple streams of data–both internal and external–and effectively log and assess different threats and vulnerabilities within their cloud infrastructure.
N2K’s Cloud SOC course is a five-hour, 100% online program that provides training for security professionals in the detection and identification of attacks on their cloud infrastructures. Learners will become familiar with network captures and logging in both the AWS and Azure instances. Additionally, learners will be prepared to conduct further vulnerability analysis and cloud inventory discovery.
Participants will gain first-hand knowledge of the implications of cloud security in SOC with instruction led by a subject matter expert and industry leader in security operations. This introductory role-based course serves as a precursor to the Critical Knowledge: SOC Analyst and the Cloud Incident Response programs.
Prerequisites
It is recommended to have some basic knowledge of security systems and controls, as well as experience working with cloud platforms like Microsoft Azure and Amazon Web Services. Practitioners with a Security+ certification or those who have completed N2K’s Critical Knowledge course are suggested.
Relevant Training
There are several options to continue training following the Cloud SOC course, including:
Who should take this course?
- Security Professionals to familiarize themselves with cloud monitoring and detection concepts
- Tier I/II SOC Analysts
- Risk and Compliance Analysts
- Cloud Practitioners
- IT and Network Administrators
Benefits of Training
Organizations participating in this offering will experience the following major benefits:
- Course taught by an industry leader in SOC
- Optional configurable Live Online training session
- Teaches to real-life scenarios and not a certification
Additional Resources
THIS OFFERING INCLUDES
An intelligent solution.
Diagnostic Assessment
Video Lessons
Practical Labs
Final Assessment
Diagnostic Assessment
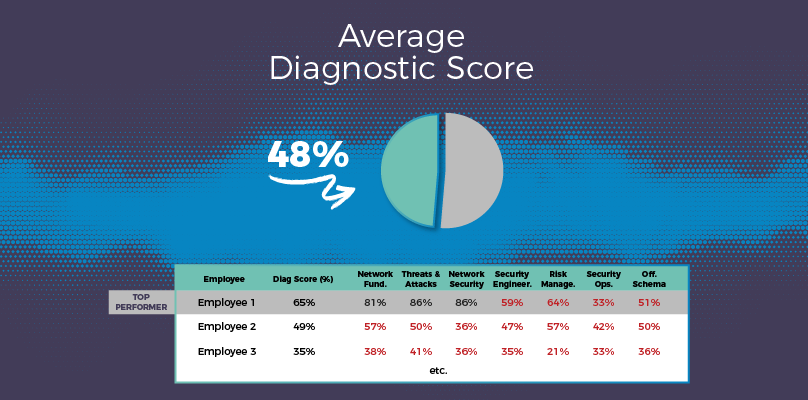
Diagnostic Assessment
Easily administer a diagnostic assessment is used to determine each team member’s strengths and weaknesses.
Video Lessons

Video Lessons
Engage with introductory videos, modular lessons, and interviews with Health IT experts.
Practical Labs

Hands-On Activities
Take-home activities and hands-on labs reinforce practical applications of security concepts.
Final Assessment

Final Assessment
Participants conclude training with a final assessment to determine improvement across knowledge and skills.
Want to learn how N2K can set up your team for success?
Course Outline
The Cloud SOC course consists of three domains that establish foundational cybersecurity knowledge on attack lifecycles and network captures, an overview of logs and log types, and effective cloud management and vulnerability analysis. Click on the sections below to see the expanded topic areas within each domain.
Domain 1: Attack Overview and Network Capture
This unit covers attack lifecycles (Cyber Kill Chain, Mitre Att&ck Framework) and network captures and logs.
- Attack Lifecycle Review
- Network Captures and Logs
Domain 2: Logs Overview and Log Types
This unit introduces logging as a whole as well as various types of logs that security analysts will need while working in the cloud.
- Log Overview
- Cloud Logging
- API Logging
- Application Logging
- Container Logs
Domain 3: Cloud Management and Vulnerability Analysis
This unit covers cloud inventory management, data discovery, and vulnerability analysis.
- Cloud Inventory and Data Discovery
- Vulnerability Analysis
This course includes:
- 5hrs of On-Demand Video Lessons
- 15 Question Diagnostic Exam
- 15 Question Final Exam
- 15 Knowledge Check Questions
- Hands-On Lab Exercises
- Live Online Session (Optional)
- Tool and Shortcut Handouts
- Performance Tracker
Why N2K?
Data-Driven
Configurable
Effective
Credible
Training aligned to NICE Framework and top certification bodies
Request Pricing
Why N2K?

DATA-DRIVEN

EFFECTIVE
Invest more deliberately and better measure training ROI

CONFIGURABLE
Training that’s tailored for your organization

CREDIBLE
Training aligned to NICE Framework and top certification bodies
Request Pricing
Cloud SOC Course FAQs
How is training delivered?
The standard training modality of the course is video-on-demand. Participants have access to all training tools including video lessons, guided labs, knowledge checks, and more within our proprietary LMS for 180-days. Live online instruction is available upon request.
Does this course train towards a certification?
No. While certain units and topics may reflect select certifications, the intended purpose of the Cloud SOC course is not to prepare for an exam but to cover the foundational attack concepts, log processes, and cloud management and vulnerability analysis practices essential for practitioners in a related security or SOC function.
Who are the instructors of the course?
- Rebecca Blair, SOC Manager in Computer Software Industry
Is a certificate of completion available?
Yes! Participants receive a digital badge once they have successfully completed the course. This badge can be displayed on social profiles or email signatures. Click here to learn more about N2K’s digital badging.

