Online Training Course
IT Security Essentials
Build critical cybersecurity knowledge and skills needed by IT teams to protect enterprise data and reduce organizational risk.
Course Overview
The role of the IT professional is changing. Technology is rapidly evolving to accommodate organizational initiatives and environmental changes, all of which require a greater emphasis on security to protect these systems throughout migration and maintenance. Consequently, IT professionals are being asked to take on more cybersecurity-related tasks, yet often lack the appropriate knowledge and skills around fundamental cybersecurity principles.
In a high-stakes environment where cybersecurity incidents or outages can affect business operations, it is vital for IT practitioners to understand cybersecurity fundamentals and how to apply best practices to minimize risks to customers, partners, and the organization.
The IT Security Essentials course is a five (5) hour, 100% online program designed to teach IT professionals the key foundational concepts of cybersecurity. The course includes video lessons, case studies, lab exercises, and 1:1 interviews with an industry expert in IT security.
More than Security Awareness Training
This course goes beyond general awareness training to address cybersecurity threats and vulnerabilities related to protecting business data and maintaining enterprise systems. We incorporate real-world examples and hands-on exercises to help put theory into practice. Following this course, the practitioner will be more knowledgeable on cybersecurity lexicon, common threats and attacks, and proper mitigation strategies.
Prerequisites
It is recommended to have some basic knowledge of IT or computer networking. However, there are no formal prerequisites for this course.
Certifications
For entry-level or transitioning talent, CompTIA’s Security+ is the perfect next step to expand their cybersecurity knowledge and credibility.
Who should take this course?
This introductory course is designed for entry-level IT professionals and help desk staff who are taking on more cybersecurity-related responsibilities by obligation or personal interest.
- IT Help Desk whose daily responsibilities have grown to include cybersecurity tasks.
- System and Network Administrators who assess security posture and implement appropriate solutions to combat ransomware and data breaches.
- IT Managers overseeing or evaluating cybersecurity-related tasks, programs, or initiatives.
- New hires in IT or cybersecurity
Benefits of Training
Organizations participating in this offering will experience the following major benefits:
- Efficiently build cybersecurity knowledge, skills, and abilities related to IT responsibilities.
- Increase confidence and ability to converse on and handle cybersecurity incidents.
- Close cyber talent gaps by upskilling or reskilling IT practitioners.
THIS OFFERING INCLUDES
An intelligent solution.
Diagnostic Assessment
Video Lessons
Practical Labs
Final Assessment
Diagnostic Assessment
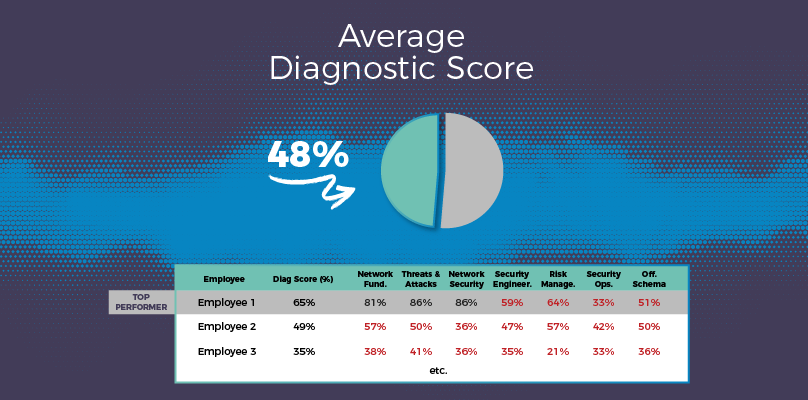
Diagnostic Assessment
Easily administer a diagnostic assessment is used to determine each team member’s strengths and weaknesses.
Video Lessons

Video Lessons
Engage with introductory videos, modular lessons, and interviews with Health IT experts.
Practical Labs

Hands-On Activities
Take-home activities and hands-on labs reinforce practical applications of security concepts.
Final Assessment

Final Assessment
Participants conclude training with a final assessment to determine improvement across knowledge and skills.
Want to learn how N2K can set up your team for success?
Course Outline
As a true foundational curriculum, the IT Security Essentials course spans five major units that establish foundational cybersecurity knowledge, examines vulnerabilities of an organization’s network and devices from internal and external threats, and common defenses to reduce risk. Click on the sections below to see the expanded topic areas within each unit.
Unit 1: Risk, Privacy, and Data Protection
Introduce (or re-introduce) learner to lexicon of cybersecurity. Discuss most important industry words and phrases to create a foundation for further learning.
- Defining Cybersecurity
- CIA Framework
- Defining Risk
- Privileged Access
- Defining Sensitive Data
- Laws, Regulations, and Compliance Initiatives in Cybersecurity
Unit 2: IoT, Cloud, and Critical Networking Protocols
Examine insecure aspects of network and device communication. Highlight the fact that many services and devices are insecure, by default; not designed with security in mind.
- The Network
- IoT Devices
- Cloud Computing
- Passwords
Unit 3: External and Internal Threats & Attack Methods
Demonstrate how attackers exploit vulnerabilities. Discuss technical, network-based attacks (MITM, Dos) and non-technical (social engineering).
- Threat Actors
- Third Parties
- Social Engineering
- Man-in-the-Middle
- DoS Attacks
- Malware
Unit 4: Software Tools, IAM, and Incident Response
Discuss common defenses against attackers and bad actors. Discuss technical defenses such as VPNs and network segmentation, but also less technical efforts such as communicating with users and coordinating other teams and business leaders.
- Network Segmentation
- Blacklisting/Whitelisting
- VPN
- Password Security
- Incident Response
- Patch Management
Unit 5: Cybersecurity Communication and Third-Party Management
Interviews with a Director of IT, discussing the major trends in IT and cybersecurity. He also discusses how IT Professionals can coordinate and communicate with the cybersecurity team and help when cybersecurity incidents do occur. Interviews help highlight the ‘soft skills’ needed by IT practitioners.
- Communicating About Cybersecurity
- Writing Cybersecurity Reports
- Connection Between IT and Cybersecurity Teams
- Communicating with Third Parties
This course includes:
- 4 hours on-demand training videos
- Practical, hands-on activities
- 15 question diagnostic exam
- 15 question final exam
- 15 knowledge check questions
- Expert interviews
- Performance Tracker
- Summary Video
- Deep-dive into notable breaches and cyber incidents
Why N2K?
Data-Driven
Relevant
Efficient
Cost-Effective
Request Pricing
Why N2K?

DATA-DRIVEN

EFFICIENT

RELEVANT

COST-EFFECTIVE
Request Pricing
Request more information on training options for your cybersecurity teams. Private classes are available.
IT Security Essentials FAQs
How is training delivered?
The standard training modality of the course is video-on-demand. Participants have access to all training tools including video lessons, guided labs, knowledge checks, and more within our proprietary LMS for 180-days. Live online instruction is available upon request.
Does this course train towards a certification?
No. While certain units and topics may reflect select certifications, the intended purpose of the IT Security Essentials course is not to prepare for an exam but to cover the foundational concepts, processes, and regulations related to cybersecurity in IT.
Who are the instructors of the course?
- Sam Meisenberg, Cybersecurity Instructor, Curriculum Developer, CISSP, Security+, CEH
- Scott McClure, Sr. Director, Technology at the Graham Holdings Company
Is a certificate of completion available?
Yes! Participants receive a digital badge once they have successfully completed the course. This badge can be displayed on social profiles or email signatures. Click here to learn more about N2K’s digital badging.

