Eternal Blue. BlueKeep. Shellshock. Spectre/Meltdown. Heartbleed. Log4j.
Did any of those names send a shiver down your spine or cause you to break out into a cold sweat?
If none of them did, it’s very possible it did for a security professional you know and boy, could they tell you truly terrifying stories about one or more of them. Some of these vulnerabilities were around decades before being discovered and exploited in the wild, while others were relatively new and required extensive analysis and a custom coding solution before the software vendor finally rolled out a patch. In some cases, an expensive upgrade and data migration was required to avoid the vulnerability altogether.
What all of these vulnerabilities have in common is that they were reported widely by the general media and used in countless fear-based marketing and sales campaigns. But depending on your organization, these vulnerabilities may have had little or no impact on the overall security infrastructure.
Certain vulnerabilities like Eternal Blue and BlueKeep affected only Windows systems, while Heartbleed could affect any Web server, but only if that server implemented OpenSSL versions 1.0.1 through 1.0.1f. Similar to the limitations of Log4j, any installations of previous or later versions of the OpenSSL were not vulnerable to Heartbleed. Shellshock is a Unix Bash shell bug that was immediately exploited across multiple high-profile targets in the wild, while the uptake on exploiting Log4j has been relatively slow despite the published proof of concepts (POCs) readily available online. And Spectre and Meltdown vulnerabilities affected Intel x86 processors from the last couple of decades!
Priorities Matter
The truth is not every vulnerability is created equal. Some may not even be applicable to one company, while that same vulnerability in another company could represent a catastrophic impact to day-to-day operations. Fear alone cannot drive security efforts, especially when it comes to remediating vulnerabilities. You need to have a deep understanding of the organization you’re protecting, particularly an up-to-date asset inventory, and a reasonable system of prioritization that takes into account both the likelihood and impact, not just the static CVE score. Otherwise, the security team will run ragged chasing potential ghosts, being overstretched and too exhausted to effectively protect an organization when an incident actually occurs. Unfortunately, this is far too often the rule than the exception.
Luckily, our friendly researchers at Recorded Future are more interested in prioritization than yelling wolf everytime a new vulnerability rolls out (spoiler alert: they always will!) They regularly publish their top ten list of security vulnerabilities most exploited by hackers in the wild, not just some potential that was discovered in a pure lab setting. Their analysis is based on metadata from open, deep, and dark web sources, not based solely on what the vendors claim, and takes into account multiple exploit vectors, whether it’s phishing, automated exploit kits, or RATs (remote access Trojans). A RAT is a piece of malware that includes a back door, allowing attackers administrative control over the computer in which it is installed.
The Top Ten (or Eleven)
Before we share their list for last month, we asked our own audience to choose which IT vendor was most exploited by hackers. These are the results we received from all of you:
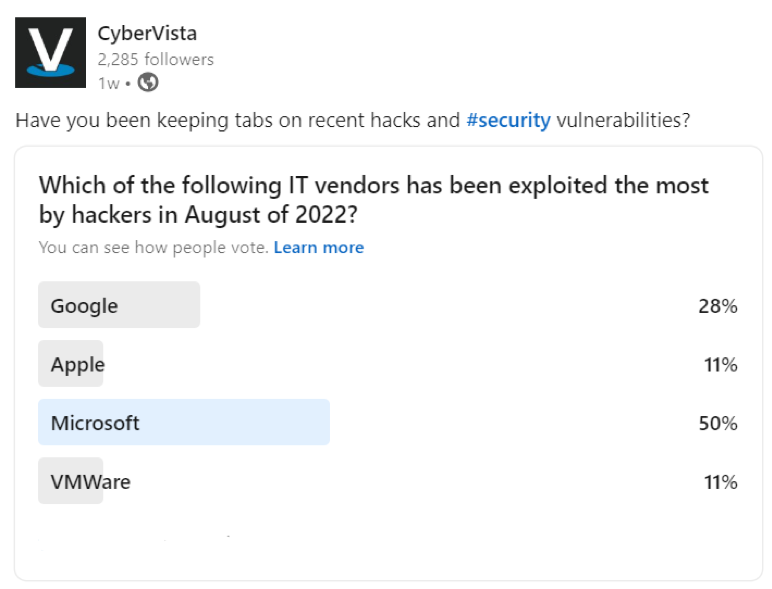
According to our audience, the IT vendor that has been exploited the most and represents the higher risk vulnerabilities is Microsoft by a mile, and then followed by Google in a distant second. Both VMWare and Apple round out the pack tied in last place. Conventional wisdom is definitely strong with these choices, as probably Microsoft and Google roll out patches almost weekly and even more often in the month of August. But what our respondents may not realize is that Apple and VMWare have some critical vulnerabilities worth looking into.
In Recorded Future’s Annual Vulnerability Report for August 2022, they listed the top 11 most commonly exploited vulnerabilities as:
- CVE-2022-2856 – Google Chromium Web browser
- CVE-2022-27255 – Realtek eCos Interface controller
- CVE-2022-32548 – DrayTek Vigor Router firmware
- CVE-2022-32893 – Apple Safari Webkit Web browser
- CVE-2022-32894 – Apple iOS, iPadOS, and macOS
- CVE-2022-34699 – Microsoft Windows and Windows Server Operating system
- CVE-2022-31656 – VMWare Workspace ONE Device management
- CVE-2022-31659 – VMWare Workspace ONE Device management
- CVE-2022-0028 – Palo Alto Networks PAN-OS Operating system
- CVE-2022-34713 – Microsoft Windows and Windows Server Operating system
- CVE-2020-14321 – Moodle Learning Management system
With an unprecedented number of patch alerts for a single piece of software, it’s no surprise that Google would be number 1. So far in 2022, Google Chrome has released over 11 new security fixes and patched its sixth zero-day vulnerability!
Although Google takes the top spot at a risk score of 99, an Apple device running its default OS and Safari browser represents a higher combined risk for those users. But if you take into account that Microsoft Windows (with two vulnerabilities at scores 91 and 79) has a higher worldwide market share than Apple iOS and OS X combined, and that the DogWalk vulnerability affects almost all versions of Windows, then you could make the case that Windows users are possibly even more vulnerable. It just depends on which of the two vendors your organization is primarily reliant!
What’s a Company To Do?
Since you can’t boil the ocean all at once, nor address all vulnerabilities the exact same ways, you need to have experts in vulnerability management to help with analysis and remediation efforts. This is one of the reasons why N2K developed the Vulnerability Assessment and Management course.
The Vulnerability Assessment and Management 5-hour online course consists of three domains that establish foundational cybersecurity knowledge on risks and threats, how to effectively manage and report vulnerabilities, and common detection and mitigation tactics:
- Risks and Threats: Explain the relationship between vulnerabilities, threats, likelihood, impact, and response in cybersecurity risk analysis within an organization, and identify and categorize the likely threats that target different types of businesses.
- Managing and Reporting Vulnerabilities: Describe the steps in vulnerability assessment, and how to collaborate with the security team and communicate with the rest of the company, and given a series of vulnerability scans, describe how to report the threats to the rest of the business.
- Detecting and Mitigating Vulnerabilities: Explain how blue and red teams use reconnaissance techniques to locate targets and identify potential vulnerabilities. Provide recommendations on remediation steps, and given an enterprise asset, choose the appropriate vulnerability tool to automate assessment. Describe and recommend mitigation techniques for common vulnerabilities.
The course includes a couple of hands-on labs to help with reinforcement, tool and shortcut handouts to reference while on the job, and interviews with security professionals that do this everyday.
It’s a Process, Not an End State
As this vulnerability list reminds us, vulnerability assessment and management isn’t just about filling in all of the cracks at once. An organization needs to evaluate the impact on its critical operations against its own risk appetite. Many automated vulnerability scanning products provide a default risk score, but this “out-of-the-box” risk doesn’t reflect the likelihood and impact of an exploit to the specific organization. Ultimately, only a human familiar with the organization’s business can do that.
Vulnerability assessment and management is not about mastering vulnerability scanners and following their detailed remediation recommendations. An organization needs to consider its unique situation. Some fixes could open new vulnerabilities, or impact operations on other systems, so vulnerability management is about tailoring the solution to the organization. A vulnerability scanner that is not configured properly for its environment could create so much noise as to overwhelm the really important vulnerabilities the organization should be prioritizing.
Vulnerability assessment and management is not a distinct process, separated from the rest of the business. Risk management, assessment, and remediation should be embedded into every aspect of business operations. Also, fixing vulnerabilities requires collaboration with many different business roles, across multiple departments and teams.
If you want to learn more about how N2K helps organizations get out of the cycle of patch and repeat, without considering the organization as a whole, let’s chat.


