By Jeff Welgan, Head of Executive Training Programs, N2K
This is the first post in a six part series about cybersecurity risk. Each week we discuss a different category of enterprise risk and how cybersecurity impacts those risks at the board and executive level.
Cybersecurity as a Risk Influencer
Focus on cybersecurity issues has skyrocketed in business and organizations over the past few years. Ray Kelly, Vice Chair of K2 Intelligence and the longest-serving NYPD Commissioner, recognized in August 2016 that, “Cyber is interwoven into everything that we do…Cyber has to be everyone’s concern and everyone’s problem.” Executives seem to agree: the number of boards who claim they actively address computer and information security increased over 40% in the last four years.
Unfortunately, many leaders confuse addressing cybersecurity with relegating it to IT professionals or the scapegoat CISO. Leaders should rethink how they are dealing and thinking about cyber issues. Directors and executives should view cyber risk as an influencer to existing risk categories they are already familiar with.
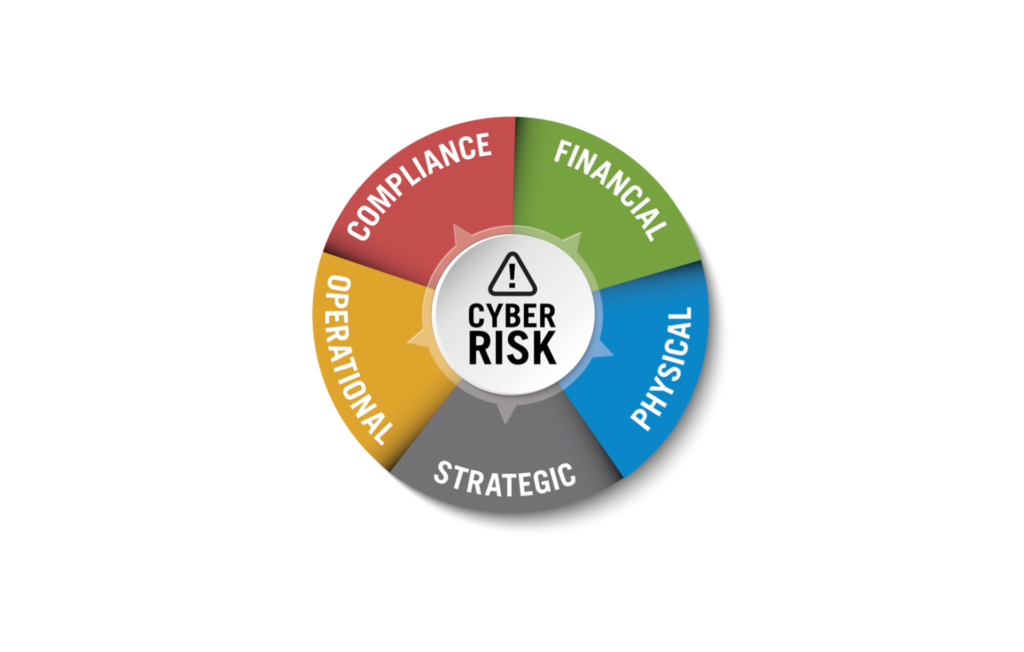
Let’s dig deeper and explain how cyber risk influences the more familiar risk areas: financial, compliance, operational, strategic, and physical. Over the next several weeks we will be visiting each of these areas of risk in more detail.
Financial Risk:
The financial cost of a cyber incident can be devastating. In 2016, the average cost of a data breach was over $7 million. These costs apply to business acquisitions as well. A massive data breach at Yahoo two years ago resulted in a staggering $1 billion discount in the sale of Yahoo to Verizon.
Compliance Risk:
Failing to comply with the latest cyber-related laws and regulations can result in financial penalties, and in some cases, leadership discipline for those directors who fail to meet their fiduciary responsibilities. At a minimum, not meeting the latest government regulations concerning cybersecurity practices may lead to action from regulators. The FTC brought charges against clothing company American Apparel in 2014 for their false claim that they had met compliance requirements. American Apparel later agreed to settle.
Strategic Risk:
Cyber incidents and even the appearance of weak security can seriously harm your brand. Negligent cybersecurity practices can cause customers to lose trust, resulting in lost business in the short term and a loss of brand asset value in the medium and long term. While evidence suggests that large companies with major breaches seem to be able to overcome negative brand impacts (largely due to costly incident response plans), the so-called Panama Papers released earlier this year have damaged the reputations and personal brands of world leaders, public figures, and major law firms.
Operational Risk:
Poor cybersecurity can lead to disruptions that could cost a significant amount of time and manpower, resulting in costly downtime for your organization. In 2012-2013, a series of attacks dubbed Operation Ababil employed DDoS (Distributed Denial of Service) tactics causing record downtime for the websites of U.S. financial institutions, including JPMorgan Chase and Bank of America.
Physical Risk:
Cyber incidents can even produce physical consequences and endanger the lives of employees, partners, and customers. In recent years cyber incidents have caused damage to assets such as industrial equipment, dams, pipelines, vehicles, and even pacemakers and insulin pumps. The most infamous example of a cyber attack to wreak havoc is Stuxnet, a highly sophisticated computer worm that undermined Iran’s nuclear program in 2010-2011 by targeting centrifuges at the Natanz Nuclear Facility.
The Five Risk Categories as Natural Disasters
To help you process and distinguish the five risk categories from each other, think of each risk category as a natural disaster. The potential damage of natural disasters should not intimidate you, but instead reassure you that the effects of natural hazards, like cyber events, can be minimized with proper planning and protections. Indeed, if we consider cyber events in the context of familiar risk areas such as natural disasters, we remove some of the intimidating aura surrounding cyber events. Cyber issues then become less intimidating, less threatening, and more manageable.
Consider these five natural disasters when you are thinking through the effects of cyber incidents on the five risk areas:
Financial Risk as a Drought
Droughts can dry up resources quickly, just like heavy financial burdens can drain a company and its stakeholders.
Compliance Risk as a Flood
Floods often move down stream, just as rules and regulations are passed down from governments. Cyber regulations and rules can pile up; they are most powerful en-masse just as floods accumulate power as waters gather. If organizations fail to act with proper due care, they can find themselves underwater with regulatory bodies. Compliance is also like a flood in that its worst effects come when there are deep cracks in basic cyber protections.
Strategic Risk as a Fire
The reputational and business loss associated with strategic risk draws intense attention from the public and media, as does the smoke and flames of a fire. Fires, like reputation loss, can spread and get out of hand very quickly.
Operational Risk as an Earthquake
Operations are the most basic foundation and function of an organization or business. An earthquake shakes foundations; makes even the most basic operations impossible to accomplish.
Physical Risk as a Volcano
Volcanoes conjure images of intense motion rolling down from the sky to result in physical destruction. Physical risk bridges the gap between cyber space and the physical world. Like volcanoes, cyber incidents resulting in physical destruction is rare, but extremely damaging.
Follow Our Series
Keep these metaphors in mind as we navigate the five risk areas over the next few weeks.
Cybersecurity now influences all of the types of risks business leaders have come to recognize over the last century. These consequences are not just meant to intimidate our leaders- in fact, they should do the opposite. By increasing cyber literacy at the board level and recognizing cyber as a risk influencer, you will significantly increase your ability to process and prioritize risks to your organization.
Cybersecurity risk can evolve quickly and can affect your entire organization. Understand your risks and plan accordingly. Need more training? Contact us. N2K provides training in the boardroom, at board and executive retreats, and in workshop settings.
Stay tuned for the next blog in this series covering Financial Risk.