Workforce Framework
for Cybersecurity
N2K maps our cybersecurity workforce development solutions to the NICE Framework to ensure your organization is building the right skills for the right roles, and helping to align your cyber strategy to the industry standard.
About the NICE Framework
The NICE Framework (NIST Special Publication 800-181) is a product from the National Initiative of Cybersecurity Education (NICE), which is led by the National Institute of Standards and Technology (NIST) in the U.S. Department of Commerce. The NICE Framework has been designed to establish and define a taxonomy and terminology to describe cybersecurity roles and their corresponding competencies (comprised of knowledge, skills, abilities, and tasks required to adequately perform those roles). The publication details 52 specific cybersecurity roles, seven (7) high-level, functional categories across cybersecurity, and 33 more specific specialty areas within the field.
On May 2, 2019, the White House released the Executive Order (EO) on America’s Cybersecurity Workforce which strongly encourages the adoption of the NICE Framework across the government, private sector, and academia.
Assessments
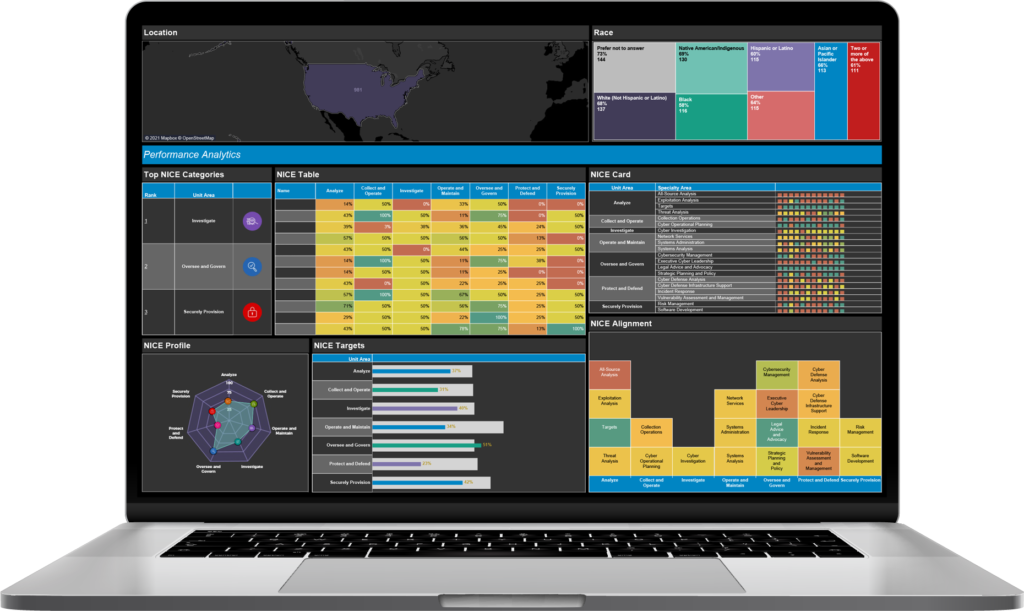
NICE Workforce Diagnostic
Gain better insight into employee competencies, outline more accurate, individualized training roadmaps, and align your people strategy to the NICE Framework, all enforced by data.
NICE Framework Categories & Training
Built upon research done by the National Initiative for Cybersecurity Education (NICE), coupled with extensive conversations of our own with several companies to understand actual job roles and organizational needs, we’ve developed an easy-to-digest guide that breaks down cyber roles within each category and relevant training solutions.
Securely Provision
Operate & Maintain
Analyze
Oversee & Govern
Protect & Defend
Collect & Operate
Investigate
Securely Provision
Job roles within the Securely Provision (SP) category specialize in the conceptualization, design, and build of secure IT systems and networks.
Risk Management: Oversees all aspects of cybersecurity risk requirements – conducting risk assessments, implementing strategies to mitigate risk, plus monitoring and documentation of risk management program – to ensure compliance.
Work Role(s): Authorizing Official, Security Control Assessor
Related N2K Training: CRISC, CISA
Software Development: Creating, designing, deploying, and testing software.
Work Role(s): Software Developer, Secure Software Assessor
Related N2K Training: Cyber Secure Coder, AWS Certified Developer: Associate, Microsoft Azure DevOps Solutions, Java SE 8 Programmer I (OCA), Deep Learning with Python
Systems Architecture: Develops system concepts and capabilities, ensures technology and external conditions (i.e. regulations) are applied into security designs and processes.
Work Role(s): Enterprise Architect, Security Architect
Related N2K Training: Cisco ENCOR, AWS Solutions Architect: Associate, AWS Solutions Architect: Professional
Technology R&D: Assesses technology and integration processes; provides, supports, and evaluates prototype capabilities and utility.
Work Role(s): Research & Development Specialist
Systems Requirement Planning: Provide consultation to clients on how to effectively translate business needs into technical solutions.
Work Role(s): Requirements Specialist
Test & Evaluation: Conducts regular systems tests to measure compliance in relation to specifications and requirements.
Work Role(s): Testing & Evaluation Specialist
Systems Development: Focuses on the development-related phases within the systems development lifecycle.
Work Role(s): Information Systems Security Developer, Systems Developer
Operate & Maintain
Responsible for support, administration, and maintenance for IT system performance and security.
Database Administration: Oversees databases and data management systems for secure storage, query, and use of data.
Work Role(s): Database Administrator, Data Analyst
Related N2K Training: Oracle Database 12c: Administration (OCA), Oracle MySQL 5.7 Database Administrator (OCP), Microsoft SQL Server 2016 (MCSA), Administering Relational Databases on Microsoft Azure
Customer Service & Technical Support: Assists and educates customers with technical-related issues relating but not limited to: installs, configurations, and troubleshooting.
Work Role(s): Technical Support Specialist
Related N2K Training: CompTIA A+ Core Exam 1, CompTIA A+ Core Exam 2, CompTIA IT Fundamentals
Network Services: Installs and maintains networks and their firewalls for both hardware and software to allow sharing of data.
Work Role(s): Network Operations Specialist
Related N2K Training: Cisco Certified Network Associate (CCNA), Cisco ENCOR
Systems Administration: Ensures CIA – confidentiality, integrity, and availability – of data’s way of installation, troubleshooting, and maintenance server configurations for both hardware and software. Responsible for access control.
Work Role(s): System Administrator
Related N2K Training: Microsoft Windows Server 2016 (MCSA), AWS SysOps Admin: Associate, Microsoft Azure Administrator (AZ-104), Microsoft 365 Security Administration
Systems Analysis: Conducts the integration, operations, and maintenance of systems security.
Work Role(s): Systems Security Analyst
Related N2K Training: CompTIA Security+, GIAC Security Essentials (GSEC)
Analyze
Cybersecurity professions under Analyze are responsible for conducting thorough reviews and evaluations of incoming cybersecurity information to assess validity and benefits for intelligence.
Threat Analysis: Monitors cybercriminal activity to collect information for supporting law enforcement or counterintelligence investigations.
Work Role(s): Warnings Analyst
Related N2K Training: EC-Council CEH, CompTIA PenTest+
Exploitation Analysis: Inspects information for vulnerabilities and exploitation risk.
Work Role(s): Exploitation Analyst
All-Source Analysis: Analyzes, synthesizes, and develops insights on threat intel from multiple sources, disciplines, and agencies.
Work Role(s): All-Source Analyst, Mission Assessment Specialist
Related N2K Training: Critical Knowledge: SOC Analyst, CompTIA CySA+
Targets: Specializes in at least one region, entity, and/or technology.
Work Role(s): Target Developer, Target Analyst
Language Analysis: Combines language, cultural, and technical expertise to effectively process and analyze cybersecurity intelligence information.
Work Role(s): Language Analyst
Oversee & Govern
Leadership, direction, and advocacy for employees and greater organization on cybersecurity initiatives and strategy.
Legal Advice & Advocacy: Provides legal advice and recommendations to leadership and staff. Acts as an advocate on policy changes and represents clients in legal briefings, proceedings, or otherwise.
Work Role(s): Cyber Legal Advisor, Privacy Compliance Manager
Training, Education, and Awareness: Oversees planning, sourcing or development, and implementation of all employee cybersecurity training initiatives.
Work Role(s): Cyber Instructional Curriculum Developer, Cyber Instructor
Cybersecurity Management: Organizes and manages the enterprise cybersecurity program.
Work Role(s): Information Systems Security Manager, COMSEC Manager
Related N2K Training: (ISC)² CISSP, ISACA CISM
Strategic Planning and Policy: Develops policies and plans for organizational cybersecurity initiatives.
Work Role(s): Cyber Workforce Developer & Manager, Cyber Policy & Strategy Planner
Executive Cyber Leadership: Leads cybersecurity and cyber-enabled teams.
Work Role(s): Executive Cyber Leadership
Related N2K Training: Resolve Risk Seminar, Resolve Executive Awareness, Resolve Cyber Breach Tabletop Exercise
Acquisition and Program/Project Management: Manages acquisitions of hardware, software, and information systems, involves project management, investment alignment, and audit.
Work Role(s): Program Manager, IT Project Manager, Product Support Manager, IT Investment/Portfolio Manager, IT Program Auditor
Related N2K Training: PMI Project Management Professional (PMP), PMI Agile Certified Practitioner (PMI-ACP), CompTIA Project+, Alexos PRINCE2 Foundation
Protect & Defend
Responsible for classification, analysis, and mitigation of cyber threats on internal systems.
Cyber Defense Analysis: Incorporates both defensive measures and intelligence to analyze and report potential and actual events within the enterprise network.
Work Role(s): Cyber Defense Analyst
Related N2K Training: EC-Council CND
Cyber Defense Infrastructure: Implement, maintain, and test infrastructure hardware and software. Monitor network for suspicious activity.
Work Role(s): Cyber Defense Infrastructure Support Specialist
Incident Response: Responds and mitigates immediate and potential threats on the network to effectively secure and/or recover enterprise data.
Work Role(s): Cyber Defense Incident Responder
Related N2K Training: Critical Knowledge: Incident Responder
Vulnerability Assessment & Management: Conducts assessments of threats and vulnerabilities, develops and/or provides recommendations for cyber threat countermeasures.
Work Role(s): Vulnerability Analyst
Related N2K Training: Critical Knowledge: Vulnerability Assessment & Management
Collect & Operate
Cybersecurity roles responsible for conducting denial and deception operations in addition to cybersecurity data that could be used for intelligence.
Collection Operations: Collects cybersecurity information using methods in accordance to the collection management process.
Work Role(s): All Source-Collection Manager, All Source-Collection Requirements Evaluation Manager
Cyber Operational Planning: Conducts strategic and operational-level planning for integrated information and cyber operations.
Work Role(s): Cyber Intel Planner, Cyber Operations Planner, Partner Integration Manager
Cyber Operations: Gathers intel on both criminal and foreign entities to effectively plan and mitigate potential cyber threats.
Work Role(s): Cyber Operator
Investigate
Responsible for examining cybersecurity activity and crimes on IT systems and networks.
Cyber Investigation: Applies various strategies and procedures to gather cybersecurity intelligence.
Work Role(s): Cyber Crime Investigator
Digital Forensics: Gathers, analyzes, and investigates digital evidence and security incidents for insights to support vulnerability mitigation.
Work Role(s): Forensics Analyst, Cyber Defense Forensics Analyst
Get more out of your cybersecurity training.
N2K’s solutions can help provide the visibility and insights you need to transform your workforce. Connect with us to learn more.