The Importance of “Getting Your Hands Dirty”
Getting Hands-On Experience with Cybersecurity Labs
A lot of eLearning platforms focus on theory, conceptual concepts, and general principles. While this is an important perspective, content is best learned with an additional hands-on aspect. In the cybersecurity field, especially, it is critical to get one’s hands “dirty.” Hands-on activities not only break up the tedium of rinse-and-repeat didactic learning, but also makes abstract concepts concrete, and helps you apply the content. Apply is the key word here. Applied learning leads to the willingness to try things out yourself and think outside the box on problems that stump others. Having both a balance of theory, and applied learning will accelerate your trajectory or your teams.
In the top-secret learning science lab at CyberVista, we have been busy brewing a potent formula of hands-on activities to assist even the greenest of n00bs and challenge the skills of the wiliest of experienced hackers. There are two flavors of labs: Guided and Problem.
Guided Labs
Guided labs are step-by-step exercises, chocked full of commentary and interesting trivia, to keep you actively engaged as you review your previous lesson(s) and dig deeper into the topics. It’s an on-the-rails experience to keep the learner and our environment safe. We don’t just play around with pseudo-tools. Remember, we are using real world hacking penetration testing tools, and they can cause serious damage if used improperly. As much as some of our lab builders in CyberVista have crashed networks and bricked hard drives while testing and learning, we don’t want that to happen to you! Even though we are on-the-rails here, our guidance keeps participants entertained and explorative, encouraging experimentation and the ability to go beyond the tasks at hand. Sometimes, the best way to learn where you are is to explore your surroundings, and we provide you with the tools and mindset to dare to strike out a new path. For example, our students will get good experience with tools like Zenmap performing standard tasks they would routinely do, but throughout the process, we provide suggested jumping-off points to use Zenmap, and other tools, in more advanced ways.
Let’s stick with the Zenmap example here. In our course, we open Zenmap, dig into the program, showcasing the basics, and then give our students the freedom to explore. We allow you to run Zenmap against web apps) or a network.
<please only scan networks or sites you have explicit written permission to scan!>
We will dig into the ability to see firewalls and server types, and we will break down the information to show the ports and other useful juicy bits with screenshots like the one below shows:
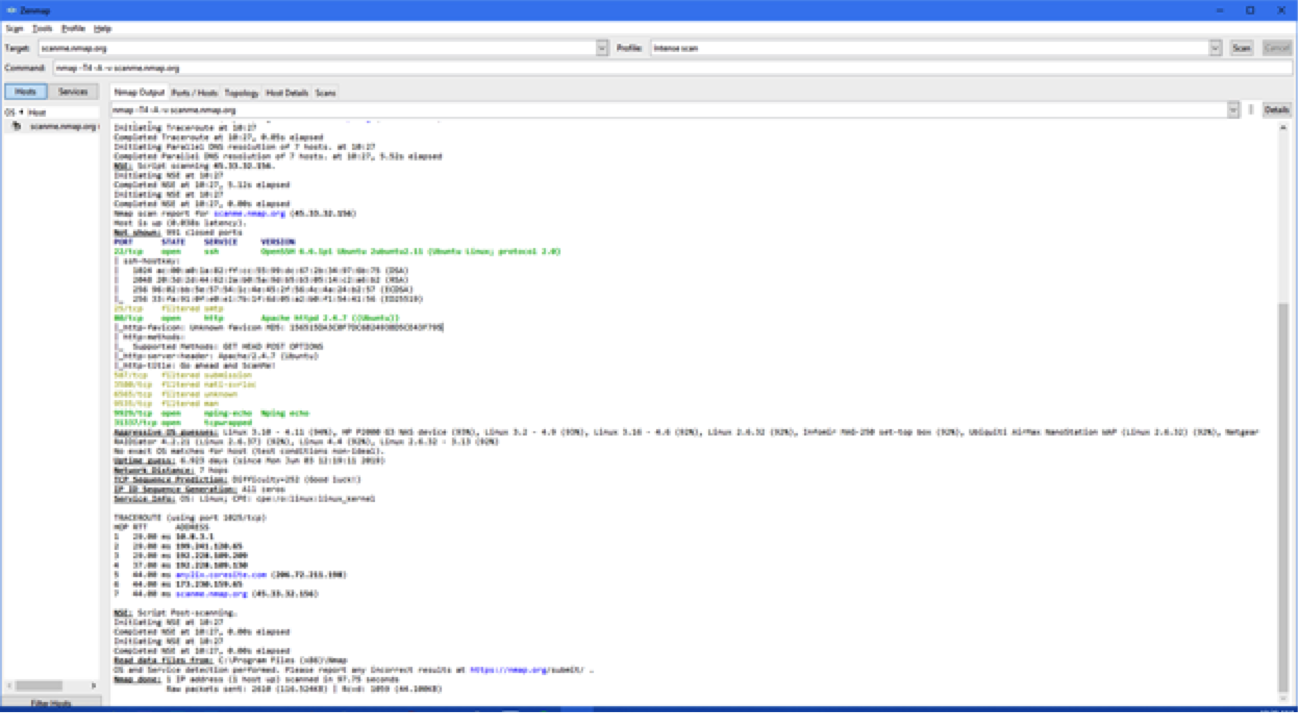 Screenshot of Zenmap showing an Intense Scan. We can go even deeper and show you the different graphical outputs of this program!
Screenshot of Zenmap showing an Intense Scan. We can go even deeper and show you the different graphical outputs of this program!
We cover both the scan types of Zenmap as well as the program outputs and how to interpret them.
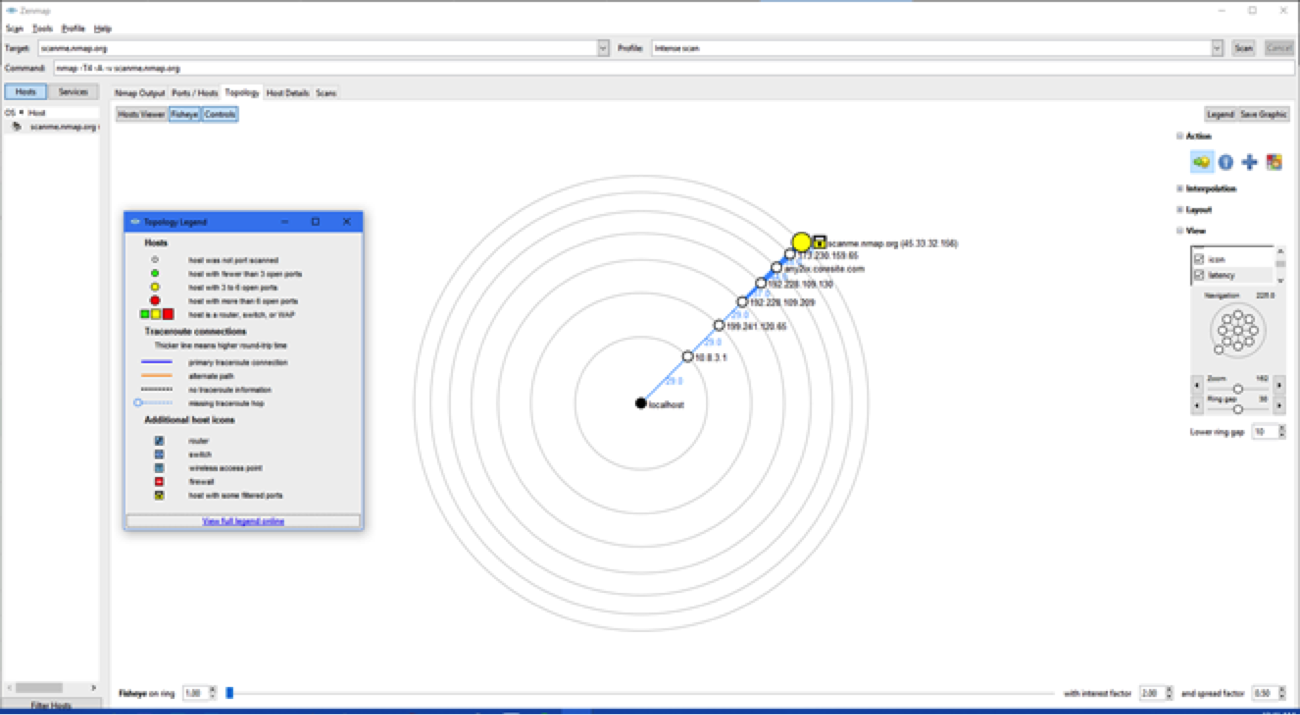 Screenshot of Zenmap showing, in this case a traceroute (or the steps it took when it went to scan scanme.nmap.org.
Screenshot of Zenmap showing, in this case a traceroute (or the steps it took when it went to scan scanme.nmap.org.
Fun fact for the whole family: you can save this as a pdf, or png, for your records when you do your scans.
Even more fun is to scan your network and it will show you all live hosts (that is, computers and IoT devices that are turned on) present on your network. It’s important to keep tabs on what is exactly on your network.
Problem Labs
Problem labs are very different; there is no recipe to follow. Students are given a problem to solve and then must reach the solution using whatever techniques and tools they have at their disposal. There are hints to help if you get stuck, but this is by your wits, and your wits alone, to figure out. This approach is rare for an eLearning platform but we believe it will make individuals and teams that much stronger.
A good example of these types of labs are capture the flag (CTF). In CTF labs, something out-of-the-ordinary has been modified or added to the environment, and you must discover what exactly it is. It could be a hidden text file or message hidden in some network packets. Only two things limit the search: the scope of the system to search and the expected format of the flag message itself. The way to succeed is by choice, and the solution we offer is only one of many paths to get there.
Labs integrate what students have learned in the preparation and encourage them to apply the practice to real-world applications. In this way, you and your team will not only talk-the-talk, but also walk-the-walk in as cybersecurity pros.
Go For It
Though it can be frustrating at times, getting lost in a lab environment and making mistakes are part of the learning journey. The ability to focus, recover, and overcome are prerequisites to a successful career in cybersecurity.
P.S., here is some homework: What?! Already?! Go download Zenmap/Nmap onto your system and use it to scan your own network and see what all is happening. https://nmap.org/download.html Till next time!
Want to learn with didactic content and applied learning? Check out our newest workforce development training program, Advance, specifically designed for cybersecurity teams.


